Interview on iNGENIOUS

The EU project iNGENIOUS has reached its end after a span of over two years.
To mark this significant milestone, BI's researchers Carsten Weinhold, Sebastian Haas, and Nils Asmussen shared insights into their contributions within the project and shed light on the potential applications of our findings in the times to come.
What was the EU project iNGENIOUS about?
Carsten Weinhold:
The iNGENIOUS project was about how the next generation of the Internet of Things (IoT) can make supply chains more efficient and secure. A total of 21 partners from the business and research sector worked together to improve and optimize the networking of industrial robots, logistics vehicles, shipping containers and even entire ports.
Although all these areas already use IoT today, a variety of isolated solutions are used in the individual sectors. The iNGENIOUS project has developed an approach to bring together the previously isolated IoT systems and their data flows across the entire supply chain. This enables an overall view that makes the management of complex supply processes easier to plan and less prone to errors.
Six use cases were selected in the project to develop and test the new technologies. An important component, for example, was the further development of 5G mobile technology for industrial applications, such as the central control and monitoring of robots in factories or the remote control of vehicles in logistics centers. Furthermore, the use of artificial intelligence methods was researched, among other things, to optimize container handling in ports. This stronger networking makes new application scenarios possible, such as the continuous monitoring of containers and their contents over the entire transport route, both on land and on the high seas.
What was the role of BI in the project and what were its specific tasks?
Carsten Weinhold:
The EU funded iNGENIOUS with a total of eight million euros distributed among the 21 project partners. With so many partners, coordination is necessary at the organizational level. But also at technical level, everyone must work together. This is where the role of the ”Technical Manager” comes in, which was taken over by the BI. As Technical Manager of the iNGENIOUS project, we were responsible for the overall technical coordination as well as the quality control for all technical project reports. For example, we had to ensure that the respective reports remained easy to read despite many authors and that they complemented each other optimally in terms of content.
BI’s second role in the project was that of ”task leader” in the development of an overall IoT architecture for the supply chain of the future. This architecture defines how existing and new technology building blocks must be designed and joined together. To do this, we worked with all partners in the project and documented the results so that everyone has a common understanding of the technical framework of the project. Most of the innovations that iNGENIOUS has produced require the interplay of multiple technical components from different partners, each working at very different levels. One example is the continuous monitoring of containers on the high seas. This involved integrating new types of sensors, a new IoT gateway for satellite communication and cloud services for data management.
And what did the BI contribute technically to the project?
Carsten Weinhold:
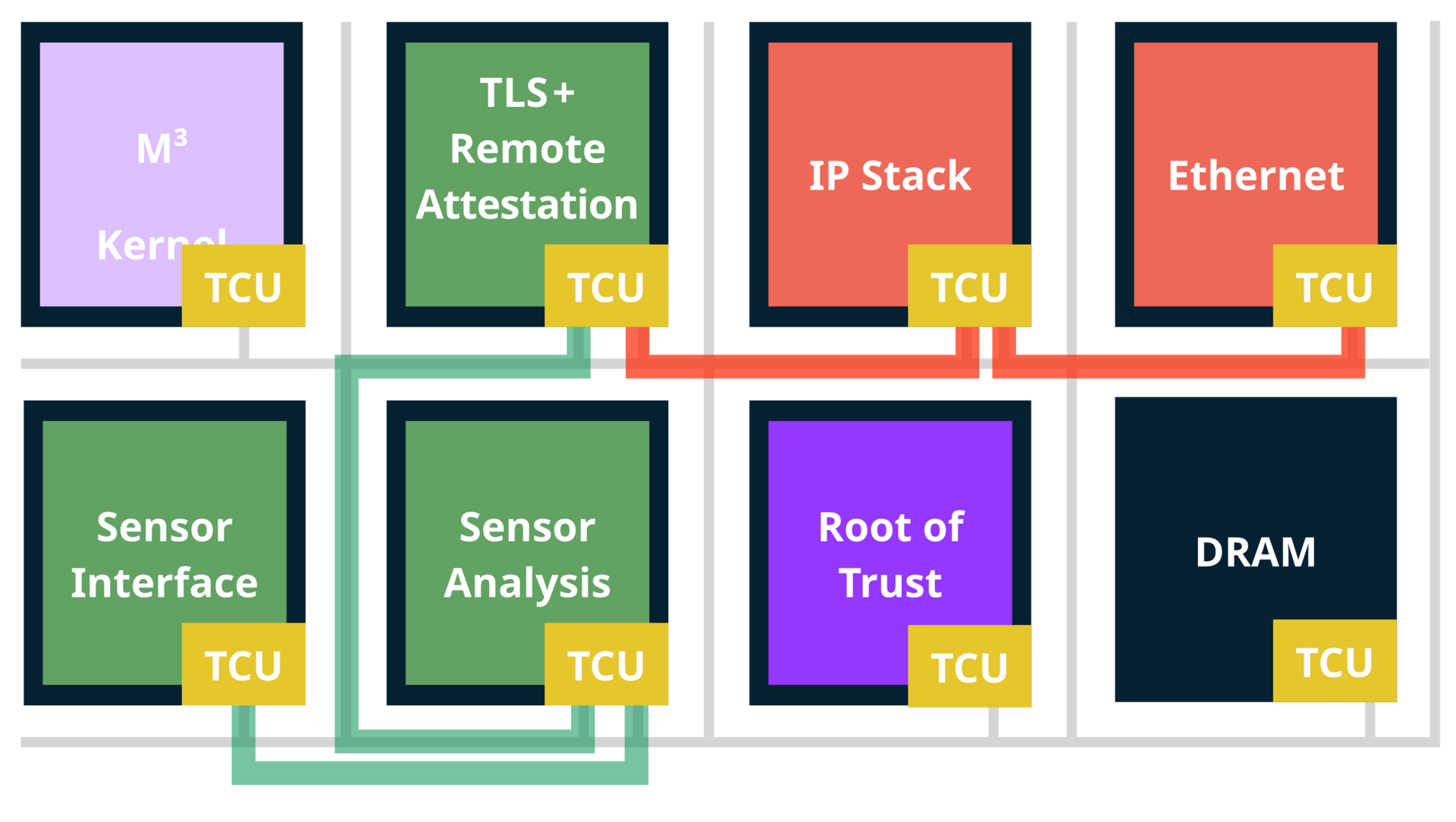
In the project, we focused on the computer systems that are built into IoT devices. For this, we contributed the M³ computer platform, which is supposed to be as secure as possible by default. M³ consists of new computer hardware on the one hand and the operating system that runs on it on the other. The special thing about M³ is that the hardware and the software are designed together and are closely coordinated.

What is so special about the hardware?
Sebastian Haas:
Unlike current computer platforms, M³ is based on a so-called ”tile” architecture. Here, components such as processors and interfaces are physically separated from the outset (security-by-design). In this way, the effects of hardware errors in the components or malware running on the processors can be minimized. In addition to the isolation of the ”tiles,” communication modules (TCU, Trusted Communication Unit) developed by us form the security basis of the computer hardware. One such TCU is provided at each ”tile” to control communication and other data access within the computer.
Within the framework of iNGENIOUS, we have built a hardware prototype for this computer architecture, which has so far only been simulated, with the help of an FPGA (Field-Programmable Gate Array). This allows us to connect our M³ computer platform to IoT sensors from project partners, for example, to vividly demonstrate project-specific use cases.
Are there any special features regarding the software?
Nils Asmussen:
The software side of M³ is a microkernel-based operating system that takes advantage of the special properties of the hardware and especially the TCU. Thus, applications are executed on different tiles for security reasons and can communicate with each other with the help of the TCU, but first need explicit permission from the operating system.
In the course of the project, this basic concept was made practicable. Although one application per tile is desirable for security reasons, in practice there are often not enough tiles for all applications. For this reason, we have extended the hardware and software side of M³ in order to be able to run several applications on one tile if necessary. This was especially challenging because we did not want to lose the strong isolation between tiles, which would have been the case with classical approaches. Furthermore, we added to the M³ platform the ability to communicate with the outside world via networks and other interfaces, which is mandatory for IoT devices.
So BI has also been working on IoT communication?
Carsten Weinhold:
Yes, another research question revolved around the security of communication on the Internet of Things. In iNGENIOUS, we worked closely with a project partner who is developing intelligent sensors to monitor railway wagons. These sensors check the axles of the wagons for potential defects and automatically report them to a control center. These damage reports are very important for the safety of railway operations. If they are suppressed, repairs do not take place and accidents can occur. If instead damage is reported that is not even present, operations are unnecessarily disrupted. Therefore, it must be ensured that the sensors communicate with the correct control center. It must also be ensured that the correct, i.e. not manipulated, software is running both on the sensors and at the railway operator.
With ”Remote Attestation,” a technology already exists to automatically check software in IoT devices and in cloud servers for manipulations. However, the use of this technology is difficult in practice. To make it easier to use, we have integrated the remote attestation technology into the widely used industry standard TLS (Transport Layer Security), which is also used in the IoT environment. The corresponding IoT systems can now be additionally secured by remote attestation with our TLS extension.
How will the project results be further used?
Carsten Weinhold:
With the improvement of the M³ system and our work on remote attestation, we have two building blocks that can make the Internet of Things more flexible and secure in the future. In principle, these building blocks are also useful for many other networked systems, for example for the network operator technology of future mobile phone generations. Another conceivable application is in the field of medical technology, where more and, above all, more secure networking can improve efficiency and quality in healthcare. We as BI believe that more security in computer and communication systems can improve trustworthiness in all these sectors.
